A website related to the Dalai Lama is hosting attack code that attempts
to surreptitiously install OS X-based spy software on the Macs of
people who visit.
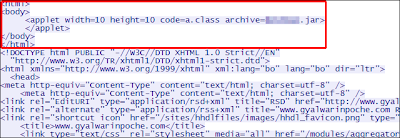
This malware is now known to be in the wild and the remote address contacted by the backdoor is now active. The Java-based exploit uses the same vulnerability as "Flashback", CVE-2012-0507. Current versions of Mac OS X and those with their browser's Java plugin disabled should be safe from the exploit. The malware dropped, Backdoor:OSX/Dockster.A, is a basic backdoor with file download and keylogger capabilities.
If it’s executed, the trojan deletes itself from the location where it was run and installs itself in the user’s home directory with the filename .Dockset. The file is not visible through Finder; however, if it’s running, it can be seen within OS X’s Activity Monitor. It creates a launch agent called mac.Dockset.deman so that the trojan will restart each time an affected user logs in. Once the trojan is active, it tries to contact the remote address itsec.eicp.net to await instructions. At the time of writing, this address is not registered, which indicates the sample may be intended simply as a test rather than an active threat.
In the case of Flashback, which was also discovered by Intego, reported 600,000 Macs were affected before both Apple and Oracle released a Java patches to remove the malware and protect against future attacks.
Although the newly-found Dockster takes advantage of an already fixed weakness, users who haven't yet updated their Macs or are running older software may still be at risk.
This malware is now known to be in the wild and the remote address contacted by the backdoor is now active. The Java-based exploit uses the same vulnerability as "Flashback", CVE-2012-0507. Current versions of Mac OS X and those with their browser's Java plugin disabled should be safe from the exploit. The malware dropped, Backdoor:OSX/Dockster.A, is a basic backdoor with file download and keylogger capabilities.
If it’s executed, the trojan deletes itself from the location where it was run and installs itself in the user’s home directory with the filename .Dockset. The file is not visible through Finder; however, if it’s running, it can be seen within OS X’s Activity Monitor. It creates a launch agent called mac.Dockset.deman so that the trojan will restart each time an affected user logs in. Once the trojan is active, it tries to contact the remote address itsec.eicp.net to await instructions. At the time of writing, this address is not registered, which indicates the sample may be intended simply as a test rather than an active threat.
In the case of Flashback, which was also discovered by Intego, reported 600,000 Macs were affected before both Apple and Oracle released a Java patches to remove the malware and protect against future attacks.
Although the newly-found Dockster takes advantage of an already fixed weakness, users who haven't yet updated their Macs or are running older software may still be at risk.



Post a Comment
I'm certainly not an expert, but I'll try my hardest to explain what I do know and research what I don't know. Be sure to check back again , after moderation i do make every effort to reply to your comments .